搜索到
16
篇与
的结果
-
 OpenCV笔记之阈值(二值化)处理 一共有5个方法• cv2.THRESH_BINARY(超过阈值部分取最大值, 如超过了阈值127变为255)• cv2.THRESH_BINARY_INV(反转上面的,可以理解为上面的颜色反转)• cv2.THRESH_TRUNC (截断,大于阈值部分设置阈值,比如大于127的就设置为127)• cv2.THRESH_TOZERO (大于阈值部分保持不变,小于等于阈值的全为0)• cv2.THRESH_TOZERO_INV(反转上面的,小于阈值不变,大于等于阈值为0)ret,thresh1 = cv2.threshold(gray,127,255,cv2.THRESH_BINARY) ret,thresh2 = cv2.threshold(gray,127,255,cv2.THRESH_BINARY_INV) ret,thresh3 = cv2.threshold(gray,127,255,cv2.THRESH_TRUNC) ret,thresh4 = cv2.threshold(gray,127,255,cv2.THRESH_TOZERO) ret,thresh5 = cv2.threshold(gray,127,255,cv2.THRESH_TOZERO_INV)from matplotlib import pyplot as plt #thresh1在上面 titles = ['BINARY','BINARY_INV','TRUNC','TOZERO','TOZERO_INV'] images = [thresh1, thresh2, thresh3, thresh4, thresh5] for i in range(5): plt.subplot(2, 3, i+1) plt.imshow(images[i]) plt.title(titles[i]) plt.show() 滤波:#均值滤波 对一个3*3的像素颜色进行平均化 img=cv2.blur(img,(3,3)) #方框滤波 和均值滤波基本一样,-1是固定写法(颜色通道),normalize是处理像素颜色加起来不会越界 #不做处理的话 越界大于255就会用255来处理 img2=cv2.boxFilter(img,-1,(3,3),normalize=True) #高斯滤波的卷积核里的数值是满足高斯分布,相当于更重视中间的 img3=cv2.GaussianBlur(img,(3,3),1) # cv_show(img3) #中值滤波 取3*3范围内的中间数 img4=cv2.medianBlur(img,3)
OpenCV笔记之阈值(二值化)处理 一共有5个方法• cv2.THRESH_BINARY(超过阈值部分取最大值, 如超过了阈值127变为255)• cv2.THRESH_BINARY_INV(反转上面的,可以理解为上面的颜色反转)• cv2.THRESH_TRUNC (截断,大于阈值部分设置阈值,比如大于127的就设置为127)• cv2.THRESH_TOZERO (大于阈值部分保持不变,小于等于阈值的全为0)• cv2.THRESH_TOZERO_INV(反转上面的,小于阈值不变,大于等于阈值为0)ret,thresh1 = cv2.threshold(gray,127,255,cv2.THRESH_BINARY) ret,thresh2 = cv2.threshold(gray,127,255,cv2.THRESH_BINARY_INV) ret,thresh3 = cv2.threshold(gray,127,255,cv2.THRESH_TRUNC) ret,thresh4 = cv2.threshold(gray,127,255,cv2.THRESH_TOZERO) ret,thresh5 = cv2.threshold(gray,127,255,cv2.THRESH_TOZERO_INV)from matplotlib import pyplot as plt #thresh1在上面 titles = ['BINARY','BINARY_INV','TRUNC','TOZERO','TOZERO_INV'] images = [thresh1, thresh2, thresh3, thresh4, thresh5] for i in range(5): plt.subplot(2, 3, i+1) plt.imshow(images[i]) plt.title(titles[i]) plt.show() 滤波:#均值滤波 对一个3*3的像素颜色进行平均化 img=cv2.blur(img,(3,3)) #方框滤波 和均值滤波基本一样,-1是固定写法(颜色通道),normalize是处理像素颜色加起来不会越界 #不做处理的话 越界大于255就会用255来处理 img2=cv2.boxFilter(img,-1,(3,3),normalize=True) #高斯滤波的卷积核里的数值是满足高斯分布,相当于更重视中间的 img3=cv2.GaussianBlur(img,(3,3),1) # cv_show(img3) #中值滤波 取3*3范围内的中间数 img4=cv2.medianBlur(img,3) -
 python加密库Crypto AES和rsa 先安装Cryptopip install pycryptodome演示mode模式为ecb的key要16位或者key和data都要byte类型import base64 from Crypto.Cipher import AES from Crypto.Util.Padding import pad def encrypt_data(text): cry = AES.new(key=("227V2xYeHTARSh1R").encode("utf-8"), mode=AES.MODE_ECB) res=(cry.encrypt(pad(text.encode("utf-8"),AES.block_size, style='pkcs7'))) print(base64.b64encode(res).decode("utf-8")) def decrypt_data(text): key = ("aiding6666666666").encode("utf-8") cry = AES.new(key=key, mode=AES.MODE_ECB) result = str(cry.decrypt(base64.b64decode(text)),"utf-8") return resultAes key长度不固定加密实现-库推荐-aes-everywhere安装pip install aes-everywhere用法 from AesEverywhere import aes256 # encryption encrypted = aes256.encrypt('TEXT', 'key') print(encrypted) # decryption print(aes256.decrypt(encrypted, 'key'))rsafrom Crypto.PublicKey import RSA from Crypto.Cipher import PKCS1_v1_5 as Cipher_pkcs1_v1_5 pk="-----BEGIN RSA PRIVATE KEY-----\nMIIEpAIBAAKCAQEAy5R1R2yM5jPPvkO2F47qVqMkYj7o92DF8y1yMkCSxY1WwqG0\ndCdUZTnaoBuAz99wGt55oGLcdalV71nPUiGWs/b6GzVN5v72baz/Q2OxHtkrFKqL\nVX16LW31cW9hAntN84RCbvTeB0MNV+SHmXjIf17OQLCtDKHBZWZ5NKyqFstO+KOd\nu32d2jsw+DT5lOBzDUBk/wUw2KyFJVx7eK6sSXEyWqBk2nxMRDNYixIEN1V1EBSq\nf+OwKK5Mxi04r38+Qog8z03/t/u6CfAOWVmi+MdrD1VHXv/P7bnFlgRcLzKwK1QL\nTSLBE1PrMmNNj0oRjByhMoI9tY5X6mRBqLyDhwIDAQABAoIBAGO++RmGO6D9CNAJ\n4Bm52eKaK5UBiubOIR8NiNLLZb5qinRxg3eX35d7Wb2xzBLNwOFBWSl21trFncfY\n4qY0s+C4ZYHYQ7Om/7nsFeQAYAOj1yJYj01TXf4NTsGGF2t+W8qxZlV0H6dCOLL0\nU2YkUmRp4Le8eQVj6dyTcVaYNPxWQBnb9ZOEIEvEjeoO/DD7CCmt7LDCey9KrTQl\nAvuc2nN6uRV1Wfm0P8conKPJtVdgzMvJujNdpz+bBDqwsqgeCICjs/hSCNO81VH3\nDD7J0mG2OHqowOVqagoDHpBprHOUKxAeTs9I0KEL+hEI4zXCDL69+Xs6azuts733\nzSOmwxkCgYEA25czfPVxxcK685LhaAvwbmzWHqNp07ytRNGf+Aww6OdgWkdgPy0n\n20Gkg0HAqsxGcgZJk6cAkOy5hBLNHpHlGbeWFi+62lVNYUv3hAxumtiPyBMu7avE\nZQCTXND1H1f/2enRDJRxQsR8y/SX1ivmC5U6fx7hbpKxnXyRHnvSlk8CgYEA7VWp\nhLNkn4AEaPPW0TknwKG40At/hjecX2zWAyZVt4ydDSeKgMEOUdmvGGlSCrefAl0n\nPTfM9SdIDcO5OTa2wUayKLIsrb6TDnG6KXXN6z3HR3Q4qKJbG83eaMYDqqziPPV+\nxzRVWShI3EGwkLczASmiYy+sEAT0OkxP59xTKUkCgYBgaGjFkukJfy4fJDxsNtmv\nUX9MYkhjGrIjxbjq6UdL6dGGsVGTSxr1i0NUETkqg5bmFtaUybxY5GWqk6qUok8o\nVE7DnN73Xn4jmnun8OFagHvXxnxTApeuFGueU2tbAIKmxJ3wXPfA7Y0w6kkDUbCl\nIzZUe1VT+3mZgAgijxBsxwKBgQDNytiJ62/V6hBo3P6pPtEcdF6nb0DtpazfBaVw\n572twaywqlermzsKeCIenbx49I1ZZGLQ72C2NpCA9vTWCn5fiyiSpyScp0ImZTDS\nIIckctYoPDug5d7wdgtjeEfXp78osopyuwtCmu7Kpd8vLNt6J5raPI0K+vC22FL1\nLpOhmQKBgQCFeU448fL87N1MjMyusi8wJ5MLcn+kHbLTtpskTpfQM2p3Cnp4oL+7\nBI4AlXlKItV37rJIjZxQgLWhGoTZPplZaW4ooJCFJbazce5ua5fnsFS0oXhDN7uw\njaq+v5t8G6gFS09hEa4kz9O53t/7UGuQqh0Bxb0cJ9iNeAlhagvBDQ==\n-----END RSA PRIVATE KEY-----" # rsa长加密 def rsa_long_encrypt(msg, pub_key_str, length=100): """ 单次加密串的长度最大为 (key_size/8)-11 1024bit的证书用100, 2048bit的证书用 200 """ pubobj = RSA.importKey(pub_key_str) pubobj = Cipher_pkcs1_v1_5.new(pubobj) res = [] for i in range(0, len(msg), length): res.append( str( base64.b64encode(pubobj.encrypt( msg[i:i + length].encode(encoding="utf-8"))), 'utf-8' ) ) return "".join(res) if __name__ == '__main__': str1='{"currency":"USD","departureDate":"2022-09-01","daysBeforeDeparture":0,"daysAfterDeparture":0,"departurePlace":"BKK","arrival":"FUK","oneway":1,"adultCount":1,"childCount":0,"infantCount":0,"returnDate":"","requestId":"1GOL7USNECUC-1660567920922","sessionId":"","_signature":"d5f6afe8c65d58543e3baf55518939a4c4d509ae2d6ee97a74f0d7059f9b9416"}' pubkey = '-----BEGIN PUBLIC KEY-----\nMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAok58IrYXjeFjb6hPgrcv\nKis43ARDVIqowS2AJKivDp4+8uKDCWnjzBZTsuVvwKPzvVCxBzON2/DPpHU3wnRt\ndKSVzWju7HMKhuLxe04FsVw8+xvZTmguBj4jTczNLSLjK13lQr46J8j7JrmVUlPq\nGxIL/Bd3HNAIFuarZQkDsgx5fvdNrMbmT4edr1b3A8wRkhfo9tuE5Tmlx0YVUwyb\nzcI6hgLggCfNwwaClXyBt08NbGSIBcKYKjiQErND0EOnWcGyto7EhkpgGRfAeESo\n3hbmsiabThLd4t9iOWVHFSl+7B0q+1IGFjSo9qkvNdMUI4ZYdIKq+nCHufpuFMl7\nSwIDAQAB\n-----END PUBLIC KEY-----' print(str1) cipher_text = rsa_long_encrypt(str1,pubkey) print(cipher_text) # rsa长解密 def rsa_long_decrypt(msg,priv_key_str, length=172): """ 1024bit的证书用128,2048bit证书用256位 """ privobj = RSA.importKey(priv_key_str) privobj = Cipher_pkcs1_v1_5.new(privobj) res = [] for i in range(0, len(msg), length): res.append( str( privobj.decrypt( base64.b64decode(msg[i:i + length]) , 'xyz'), 'utf-8' ) ) print(res) return "".join(res) # 解密 def rsaDecrypt(text): decodeStr = base64.b64decode(text) # cipher_text是上面rsa加密的内容 prikey = Cipher_pkcs1_v1_5.new(RSA.importKey(pk)) encry_text = prikey.decrypt(decodeStr, b'rsa') encry_value = encry_text.decode('utf8') print(encry_value)
python加密库Crypto AES和rsa 先安装Cryptopip install pycryptodome演示mode模式为ecb的key要16位或者key和data都要byte类型import base64 from Crypto.Cipher import AES from Crypto.Util.Padding import pad def encrypt_data(text): cry = AES.new(key=("227V2xYeHTARSh1R").encode("utf-8"), mode=AES.MODE_ECB) res=(cry.encrypt(pad(text.encode("utf-8"),AES.block_size, style='pkcs7'))) print(base64.b64encode(res).decode("utf-8")) def decrypt_data(text): key = ("aiding6666666666").encode("utf-8") cry = AES.new(key=key, mode=AES.MODE_ECB) result = str(cry.decrypt(base64.b64decode(text)),"utf-8") return resultAes key长度不固定加密实现-库推荐-aes-everywhere安装pip install aes-everywhere用法 from AesEverywhere import aes256 # encryption encrypted = aes256.encrypt('TEXT', 'key') print(encrypted) # decryption print(aes256.decrypt(encrypted, 'key'))rsafrom Crypto.PublicKey import RSA from Crypto.Cipher import PKCS1_v1_5 as Cipher_pkcs1_v1_5 pk="-----BEGIN RSA PRIVATE KEY-----\nMIIEpAIBAAKCAQEAy5R1R2yM5jPPvkO2F47qVqMkYj7o92DF8y1yMkCSxY1WwqG0\ndCdUZTnaoBuAz99wGt55oGLcdalV71nPUiGWs/b6GzVN5v72baz/Q2OxHtkrFKqL\nVX16LW31cW9hAntN84RCbvTeB0MNV+SHmXjIf17OQLCtDKHBZWZ5NKyqFstO+KOd\nu32d2jsw+DT5lOBzDUBk/wUw2KyFJVx7eK6sSXEyWqBk2nxMRDNYixIEN1V1EBSq\nf+OwKK5Mxi04r38+Qog8z03/t/u6CfAOWVmi+MdrD1VHXv/P7bnFlgRcLzKwK1QL\nTSLBE1PrMmNNj0oRjByhMoI9tY5X6mRBqLyDhwIDAQABAoIBAGO++RmGO6D9CNAJ\n4Bm52eKaK5UBiubOIR8NiNLLZb5qinRxg3eX35d7Wb2xzBLNwOFBWSl21trFncfY\n4qY0s+C4ZYHYQ7Om/7nsFeQAYAOj1yJYj01TXf4NTsGGF2t+W8qxZlV0H6dCOLL0\nU2YkUmRp4Le8eQVj6dyTcVaYNPxWQBnb9ZOEIEvEjeoO/DD7CCmt7LDCey9KrTQl\nAvuc2nN6uRV1Wfm0P8conKPJtVdgzMvJujNdpz+bBDqwsqgeCICjs/hSCNO81VH3\nDD7J0mG2OHqowOVqagoDHpBprHOUKxAeTs9I0KEL+hEI4zXCDL69+Xs6azuts733\nzSOmwxkCgYEA25czfPVxxcK685LhaAvwbmzWHqNp07ytRNGf+Aww6OdgWkdgPy0n\n20Gkg0HAqsxGcgZJk6cAkOy5hBLNHpHlGbeWFi+62lVNYUv3hAxumtiPyBMu7avE\nZQCTXND1H1f/2enRDJRxQsR8y/SX1ivmC5U6fx7hbpKxnXyRHnvSlk8CgYEA7VWp\nhLNkn4AEaPPW0TknwKG40At/hjecX2zWAyZVt4ydDSeKgMEOUdmvGGlSCrefAl0n\nPTfM9SdIDcO5OTa2wUayKLIsrb6TDnG6KXXN6z3HR3Q4qKJbG83eaMYDqqziPPV+\nxzRVWShI3EGwkLczASmiYy+sEAT0OkxP59xTKUkCgYBgaGjFkukJfy4fJDxsNtmv\nUX9MYkhjGrIjxbjq6UdL6dGGsVGTSxr1i0NUETkqg5bmFtaUybxY5GWqk6qUok8o\nVE7DnN73Xn4jmnun8OFagHvXxnxTApeuFGueU2tbAIKmxJ3wXPfA7Y0w6kkDUbCl\nIzZUe1VT+3mZgAgijxBsxwKBgQDNytiJ62/V6hBo3P6pPtEcdF6nb0DtpazfBaVw\n572twaywqlermzsKeCIenbx49I1ZZGLQ72C2NpCA9vTWCn5fiyiSpyScp0ImZTDS\nIIckctYoPDug5d7wdgtjeEfXp78osopyuwtCmu7Kpd8vLNt6J5raPI0K+vC22FL1\nLpOhmQKBgQCFeU448fL87N1MjMyusi8wJ5MLcn+kHbLTtpskTpfQM2p3Cnp4oL+7\nBI4AlXlKItV37rJIjZxQgLWhGoTZPplZaW4ooJCFJbazce5ua5fnsFS0oXhDN7uw\njaq+v5t8G6gFS09hEa4kz9O53t/7UGuQqh0Bxb0cJ9iNeAlhagvBDQ==\n-----END RSA PRIVATE KEY-----" # rsa长加密 def rsa_long_encrypt(msg, pub_key_str, length=100): """ 单次加密串的长度最大为 (key_size/8)-11 1024bit的证书用100, 2048bit的证书用 200 """ pubobj = RSA.importKey(pub_key_str) pubobj = Cipher_pkcs1_v1_5.new(pubobj) res = [] for i in range(0, len(msg), length): res.append( str( base64.b64encode(pubobj.encrypt( msg[i:i + length].encode(encoding="utf-8"))), 'utf-8' ) ) return "".join(res) if __name__ == '__main__': str1='{"currency":"USD","departureDate":"2022-09-01","daysBeforeDeparture":0,"daysAfterDeparture":0,"departurePlace":"BKK","arrival":"FUK","oneway":1,"adultCount":1,"childCount":0,"infantCount":0,"returnDate":"","requestId":"1GOL7USNECUC-1660567920922","sessionId":"","_signature":"d5f6afe8c65d58543e3baf55518939a4c4d509ae2d6ee97a74f0d7059f9b9416"}' pubkey = '-----BEGIN PUBLIC KEY-----\nMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAok58IrYXjeFjb6hPgrcv\nKis43ARDVIqowS2AJKivDp4+8uKDCWnjzBZTsuVvwKPzvVCxBzON2/DPpHU3wnRt\ndKSVzWju7HMKhuLxe04FsVw8+xvZTmguBj4jTczNLSLjK13lQr46J8j7JrmVUlPq\nGxIL/Bd3HNAIFuarZQkDsgx5fvdNrMbmT4edr1b3A8wRkhfo9tuE5Tmlx0YVUwyb\nzcI6hgLggCfNwwaClXyBt08NbGSIBcKYKjiQErND0EOnWcGyto7EhkpgGRfAeESo\n3hbmsiabThLd4t9iOWVHFSl+7B0q+1IGFjSo9qkvNdMUI4ZYdIKq+nCHufpuFMl7\nSwIDAQAB\n-----END PUBLIC KEY-----' print(str1) cipher_text = rsa_long_encrypt(str1,pubkey) print(cipher_text) # rsa长解密 def rsa_long_decrypt(msg,priv_key_str, length=172): """ 1024bit的证书用128,2048bit证书用256位 """ privobj = RSA.importKey(priv_key_str) privobj = Cipher_pkcs1_v1_5.new(privobj) res = [] for i in range(0, len(msg), length): res.append( str( privobj.decrypt( base64.b64decode(msg[i:i + length]) , 'xyz'), 'utf-8' ) ) print(res) return "".join(res) # 解密 def rsaDecrypt(text): decodeStr = base64.b64decode(text) # cipher_text是上面rsa加密的内容 prikey = Cipher_pkcs1_v1_5.new(RSA.importKey(pk)) encry_text = prikey.decrypt(decodeStr, b'rsa') encry_value = encry_text.decode('utf8') print(encry_value) -
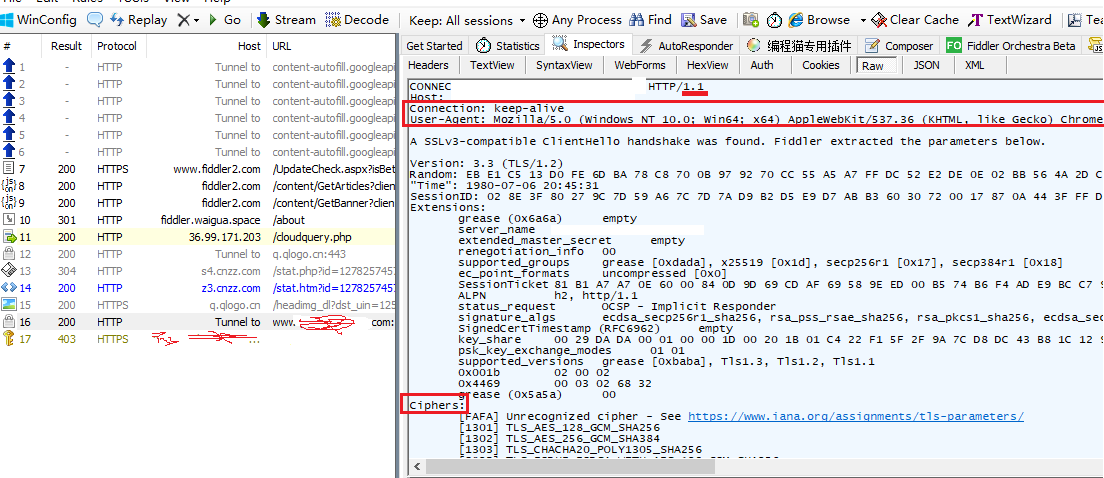
 逆向之TLS指纹 大概过tls的思路1.最主要的 设置requests tls指纹 requests.packages.urllib3.util.ssl_.DEFAULT_CIPHERS2.看发tls带了啥,一般有 http1.1和User-Agent 有的要弄上这两个 有的没检测这requests发的tls默认写http1.0 要改源码为1.1教程:先用fd抓包,看每次发请求前都有一个Tunnel,甚至还有一把小锁的图标 点进来看 写的version 3.3(TLS/1.2) 这个就是了先搞TLS指纹吧图中的Ciphers就是指纹key 但是这个是假的用小鲨鱼 wireshark抓包点Client Hello然后Cipher Suites里面的Cipher Suite 显示有16个第一个去掉,复制后面15个就行了 复制先备用打开官方的密码表网址:https://www.openssl.org/docs/man1.1.1/man1/openssl-ciphers.html循环搜索你复制的N个 Cipher Suite 然后再把右边的value粘贴下来 如图只要右边的 最后以value:value:... 拼凑成一串再在python里import requests.packages.urllib3.util.ssl_ requests.packages.urllib3.util.ssl_.DEFAULT_CIPHERS = "TLS_AES_128_GCM_SHA256:xxx:xxx:xxx" #xxx粘贴你自己弄的那些第一步就完事了 可以尝试下能跑吗 不能就继续第二步右边的CONNECT 网址 HTTP1.1 和Headers{Connecton User-Agent} 都弄上 位置在源码 python/Lib/http/client.py//可以在python里直接写这个 import http.client http.client.HTTPConnection //然后ctrl+鼠标左键单击HTTPConnection 跳转到源码位置 //第886行的这个函数->_tunnel(self) //改成下面这样 headres按需扩展 def _tunnel(self): connect_str = "CONNECT %s:%d HTTP/1.1\r\n" % (self._tunnel_host, self._tunnel_port) connect_bytes = connect_str.encode("ascii") self.send(connect_bytes) self._tunnel_headers={ "Connection":"keep-alive", "User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36" } for header, value in self._tunnel_headers.items(): header_str = "%s: %s\r\n" % (header, value) header_bytes = header_str.encode("latin-1") self.send(header_bytes) self.send(b'\r\n')改完了记得把import源码那个删除掉可以了,不写了,该干饭了
逆向之TLS指纹 大概过tls的思路1.最主要的 设置requests tls指纹 requests.packages.urllib3.util.ssl_.DEFAULT_CIPHERS2.看发tls带了啥,一般有 http1.1和User-Agent 有的要弄上这两个 有的没检测这requests发的tls默认写http1.0 要改源码为1.1教程:先用fd抓包,看每次发请求前都有一个Tunnel,甚至还有一把小锁的图标 点进来看 写的version 3.3(TLS/1.2) 这个就是了先搞TLS指纹吧图中的Ciphers就是指纹key 但是这个是假的用小鲨鱼 wireshark抓包点Client Hello然后Cipher Suites里面的Cipher Suite 显示有16个第一个去掉,复制后面15个就行了 复制先备用打开官方的密码表网址:https://www.openssl.org/docs/man1.1.1/man1/openssl-ciphers.html循环搜索你复制的N个 Cipher Suite 然后再把右边的value粘贴下来 如图只要右边的 最后以value:value:... 拼凑成一串再在python里import requests.packages.urllib3.util.ssl_ requests.packages.urllib3.util.ssl_.DEFAULT_CIPHERS = "TLS_AES_128_GCM_SHA256:xxx:xxx:xxx" #xxx粘贴你自己弄的那些第一步就完事了 可以尝试下能跑吗 不能就继续第二步右边的CONNECT 网址 HTTP1.1 和Headers{Connecton User-Agent} 都弄上 位置在源码 python/Lib/http/client.py//可以在python里直接写这个 import http.client http.client.HTTPConnection //然后ctrl+鼠标左键单击HTTPConnection 跳转到源码位置 //第886行的这个函数->_tunnel(self) //改成下面这样 headres按需扩展 def _tunnel(self): connect_str = "CONNECT %s:%d HTTP/1.1\r\n" % (self._tunnel_host, self._tunnel_port) connect_bytes = connect_str.encode("ascii") self.send(connect_bytes) self._tunnel_headers={ "Connection":"keep-alive", "User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36" } for header, value in self._tunnel_headers.items(): header_str = "%s: %s\r\n" % (header, value) header_bytes = header_str.encode("latin-1") self.send(header_bytes) self.send(b'\r\n')改完了记得把import源码那个删除掉可以了,不写了,该干饭了 -
 python让requetst库支持https2.0及修改默认的tls 除了用httpx模块,还可以魔改下requests库来自大佬Artio的分享import urllib3.util.ssl_ import requests urllib3.util.ssl_.DEFAULT_CIPHERS = ":".join( i for i in urllib3.util.ssl_.DEFAULT_CIPHERS.split(":") if not i.startswith("!")) from requests import Session from hyper.contrib import HTTP20Adapter from requests.utils import CaseInsensitiveDict _request = Session.request class MyHttp20Adapter(HTTP20Adapter): def __init__(self, *args, **kwargs): super(MyHttp20Adapter, self).__init__(*args, **kwargs) super(HTTP20Adapter, self).__init__(*args, **kwargs) def request(self, method, url, clear_headers=False, http2=False, **kwargs): if http2: self.mount("https://", MyHttp20Adapter()) if clear_headers: self.headers = CaseInsensitiveDict() result = _request(self, method=method, url=url, **kwargs) return result r=requests.Session() r.headers= { 'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36', } data = { 'page': '2' } res=request(r,method="post",url="",http2=True,data=data) print(res.text)
python让requetst库支持https2.0及修改默认的tls 除了用httpx模块,还可以魔改下requests库来自大佬Artio的分享import urllib3.util.ssl_ import requests urllib3.util.ssl_.DEFAULT_CIPHERS = ":".join( i for i in urllib3.util.ssl_.DEFAULT_CIPHERS.split(":") if not i.startswith("!")) from requests import Session from hyper.contrib import HTTP20Adapter from requests.utils import CaseInsensitiveDict _request = Session.request class MyHttp20Adapter(HTTP20Adapter): def __init__(self, *args, **kwargs): super(MyHttp20Adapter, self).__init__(*args, **kwargs) super(HTTP20Adapter, self).__init__(*args, **kwargs) def request(self, method, url, clear_headers=False, http2=False, **kwargs): if http2: self.mount("https://", MyHttp20Adapter()) if clear_headers: self.headers = CaseInsensitiveDict() result = _request(self, method=method, url=url, **kwargs) return result r=requests.Session() r.headers= { 'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36', } data = { 'page': '2' } res=request(r,method="post",url="",http2=True,data=data) print(res.text) -
 js逆向 扣代码-检测使用环境 通过代理对象的方式来修改get set代理代码const proxy = function(obj) { return new Proxy(obj, { set: (target, prop, val) => { console.log("SET>>>>", prop, prop, val) return Reflect.set(...arguments); }, get: (target, prop, r) => { console.log("GET>>>>", prop, prop, target[prop]) return target[prop] }, }) } //假设要对window进行监听 window = proxy(window)简单的获取第一层check_array=["document","window","navigator"]; function pr(check_array){ for(let a = 0;a < check_array.length; a++) { eval(check_array[a]+`=new Proxy(`+check_array[a]+`,{ get:function(k,v){ console.log("获取了",check_array[a],"里面的",v) return k[v]; } })`) } } pr(check_array)check数组可以添加更多的可能被检测的东东然后放js最上面跑一下方法2 深度递归30层(function () { function set_traverse_object(tarrget, obj, recursion_layers) { recursion_layers -= 1; console.log(); for (let prop in obj) { const value = obj[prop]; const tg_name = `${tarrget}.${prop.toString()}`; const value_type = get_value_type(value); if (value && value_type === "object" && recursion_layers >= 1) { set_traverse_object(tg_name, value, recursion_layers); continue } if (value && value.toString() !== '[object Object]') { console.log(`setter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}`); continue } console.log(`setter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}\n`) } } function new_handel(target_name, obj, number) { return new Proxy(obj, my_handler(target_name, number)) } function get_value_type(value) { if (Array.isArray(value)) { return 'Array' } return typeof value; } function my_handler(target_name, number) { return { set: function (obj, prop, value) { const value_type = get_value_type(value); const tg_name = `${target_name}.${prop.toString()}`; if (value && value_type === "object") { set_traverse_object(tg_name, value, number) } else { console.log(`setter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}`) } return Reflect.set(obj, prop, value); }, get: function (obj, prop) { const tg_name = `${target_name}.${prop.toString()}`; const value = Reflect.get(obj, prop); let value_type = get_value_type(value); if (value && value_type === 'object') { return new_handel(tg_name, value, number) } console.log(`getter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}\n`); return value } } } window = new Proxy(window, my_handler(Object.keys({window})[0], 30)); }());
js逆向 扣代码-检测使用环境 通过代理对象的方式来修改get set代理代码const proxy = function(obj) { return new Proxy(obj, { set: (target, prop, val) => { console.log("SET>>>>", prop, prop, val) return Reflect.set(...arguments); }, get: (target, prop, r) => { console.log("GET>>>>", prop, prop, target[prop]) return target[prop] }, }) } //假设要对window进行监听 window = proxy(window)简单的获取第一层check_array=["document","window","navigator"]; function pr(check_array){ for(let a = 0;a < check_array.length; a++) { eval(check_array[a]+`=new Proxy(`+check_array[a]+`,{ get:function(k,v){ console.log("获取了",check_array[a],"里面的",v) return k[v]; } })`) } } pr(check_array)check数组可以添加更多的可能被检测的东东然后放js最上面跑一下方法2 深度递归30层(function () { function set_traverse_object(tarrget, obj, recursion_layers) { recursion_layers -= 1; console.log(); for (let prop in obj) { const value = obj[prop]; const tg_name = `${tarrget}.${prop.toString()}`; const value_type = get_value_type(value); if (value && value_type === "object" && recursion_layers >= 1) { set_traverse_object(tg_name, value, recursion_layers); continue } if (value && value.toString() !== '[object Object]') { console.log(`setter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}`); continue } console.log(`setter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}\n`) } } function new_handel(target_name, obj, number) { return new Proxy(obj, my_handler(target_name, number)) } function get_value_type(value) { if (Array.isArray(value)) { return 'Array' } return typeof value; } function my_handler(target_name, number) { return { set: function (obj, prop, value) { const value_type = get_value_type(value); const tg_name = `${target_name}.${prop.toString()}`; if (value && value_type === "object") { set_traverse_object(tg_name, value, number) } else { console.log(`setter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}`) } return Reflect.set(obj, prop, value); }, get: function (obj, prop) { const tg_name = `${target_name}.${prop.toString()}`; const value = Reflect.get(obj, prop); let value_type = get_value_type(value); if (value && value_type === 'object') { return new_handel(tg_name, value, number) } console.log(`getter hook->${tg_name}; value-> ${value}; typeof-> ${value_type}\n`); return value } } } window = new Proxy(window, my_handler(Object.keys({window})[0], 30)); }());